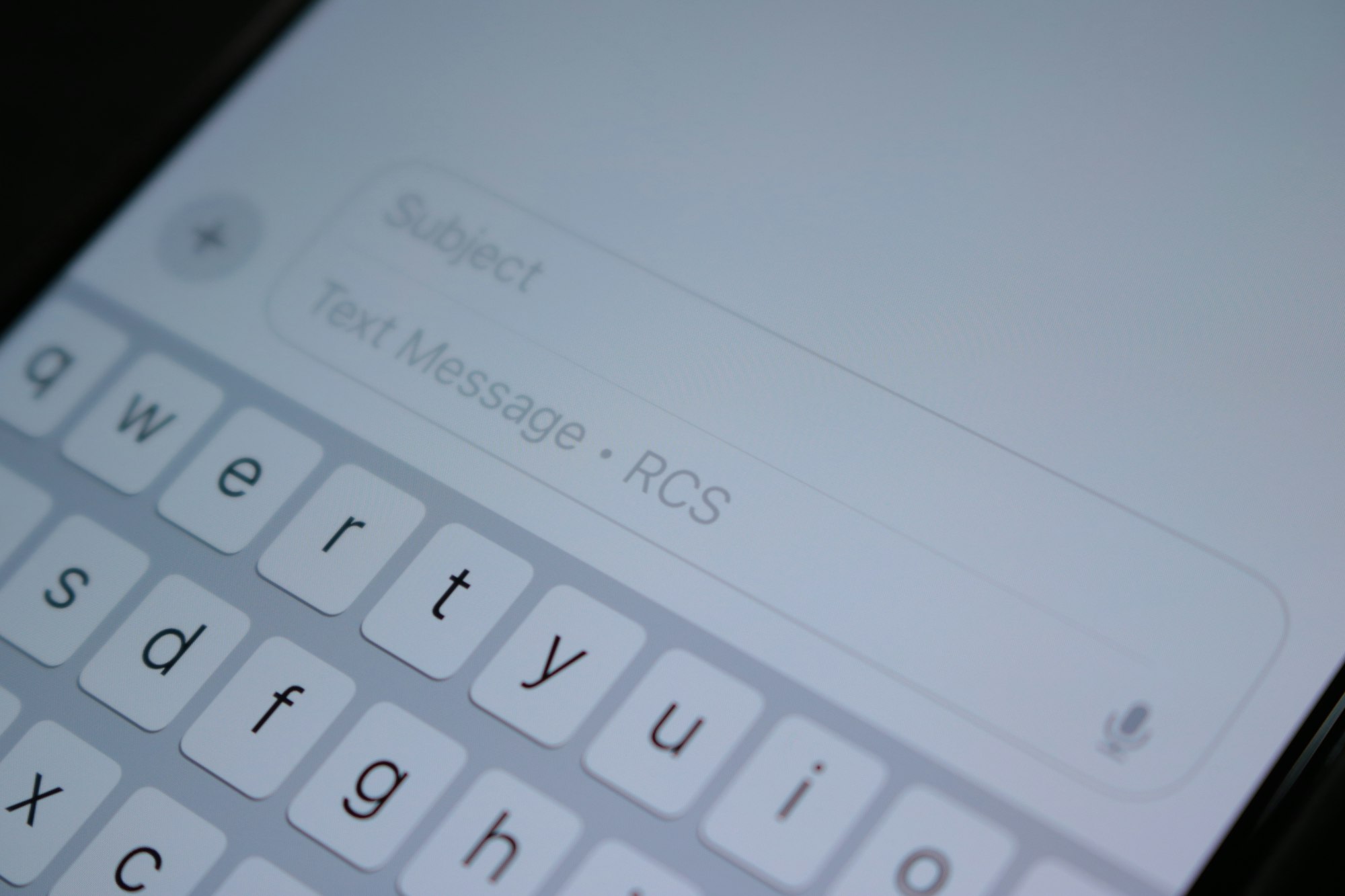
Apple has begun testing end-to-end encryption for RCS messages in the iOS 26.4 beta. While initial reports suggested the feature would arrive with iOS 26.3, it is now slated for a later public release.
The developer version of the iOS 26.4 beta was released on Monday. In a blog post, Apple confirmed the testing: “RCS end-to-end encryption is now available for testing in this beta.”
This would mean only the sender and the recipient can read the messages while they’re in transit—not the carrier, the platform provider, or anyone in the middle. Apple says conversations labeled as encrypted in the beta are protected that way, and this testing will not be available for all devices and carriers.
Apple also states that, for now, “RCS encryption is available for testing between Apple devices and is not yet testable with other platforms.” However, it added that the feature won’t be part of the iOS 26.4 update, when it goes out but "will be available to customers in a future software update for iOS, iPadOS, macOS, and watchOS.”
This update highlights a major weakness cross-platform texting has had. For years, only iMessage conversations between Apple users had end-to-end encryption; once messages enter an Android device from an Apple device, the security level drops to whatever the carrier and the RCS standard support.
The GSM Association announced last year it would add end-to-end encryption to the RCS through the Universal Profile 3.0, built on Messaging Layer Security (MLS). Apple’s move suggests the company is now aligning with that standard.
If implemented, this could close the long-standing gap between iPhones and Androids. This means texting from an iPhone device to an Android would have the same level of security as texting an iPhone device using iMessage.
This beta update also comes with additional security changes. Apps can now opt into Memory Integrity Enforcement, a system Apple introduced last year to help safeguard against sophisticated spyware by strengthening memory safety protections across critical areas of the operating system.
There are also reports that suggest that Stolen Device Protections may be enabled by default in future updates, adding biometric checks and a one-hour delay before sensitive account changes can be made.