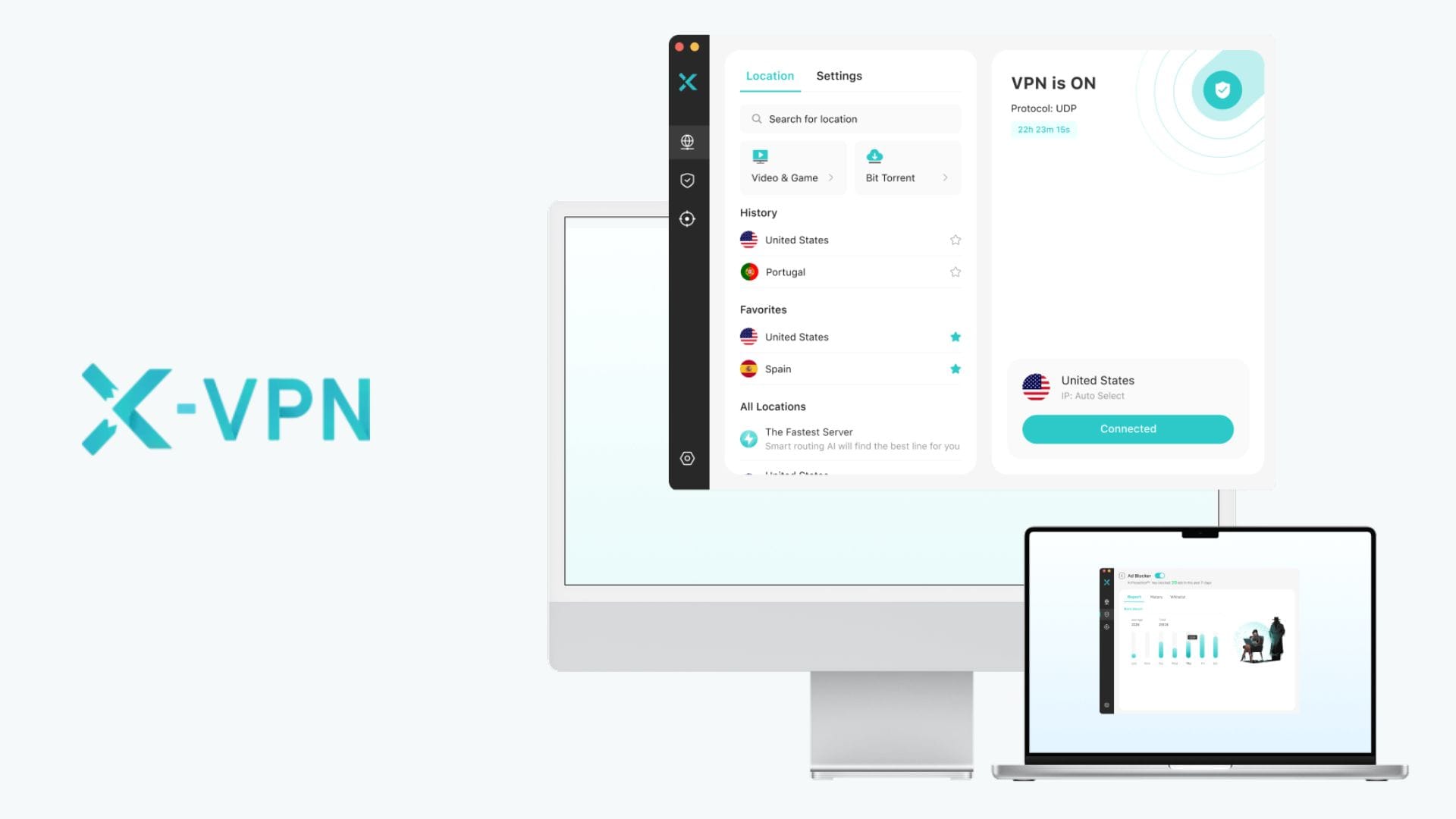
Most VPNs ask for trust. X-VPN invites you to test it. In a digital landscape where user data is routinely tracked, logged, and sold, X-VPN offers a way to verify what it promises: no logs, no leaks, and no assumptions.
This guide walks through the features that let users see, not just believe, how X-VPN protects privacy across platforms—with practical examples, technical clarity, and transparent disclosures.
Start with a Leak Test: See What X-VPN Hides

Before connecting to X-VPN, visit an independent leak test site like dnsleaktest, browserleaks, or ipleak. Take note of your visible IP address, DNS provider, geolocation, and WebRTC fingerprint.
Then, activate X-VPN. Run the same tests again.
What changes? If working properly, X-VPN should mask your IP, reroute DNS queries through encrypted servers, and eliminate identifiers from WebRTC tests.
Even when using a VPN, poorly configured services can still leak parts of your traffic. That could expose your real IP address or the websites you access through DNS queries. X-VPN’s Private DNS ensures that these lookups never leave the encrypted tunnel.
According to X-VPN’s Trust Center (Sep 2025), its system avoids third-party DNS entirely. Instead, DNS resolution is handled inside RAM-only infrastructure and cleared immediately after use.
Stay Covered: Kill Switch Prevents Accidental Exposure

Connection dropouts happen without warning—especially on public Wi-Fi or mobile data. In those moments, your real IP and traffic can slip through. That’s where Kill Switch comes in.
Once enabled, Kill Switch blocks all internet access the instant a VPN connection is lost. It’s automatic, no buttons to press.
Available for free on Android and iOS, and built into X-VPN premium desktop versions, it’s easy to verify. Disconnect the VPN manually and try visiting a website. You shouldn’t be able to reach anything until the VPN reconnects.
For travelers, remote workers, and journalists, this matters. A brief dropout while filing a story or accessing private platforms could reveal sensitive location or identity data.
“We believe privacy should be passive, not optional,” says Sandra Mitchell, Tech Writer at X-VPN. “Kill Switch ensures users stay protected—even when connections don't.”
Encryption That Holds Up to Scrutiny
Your traffic—emails, messages, and searches—shouldn’t be visible to anyone else. X-VPN encrypts all data with AES-256-GCM, a widely respected algorithm used by banks and government agencies. It's always on, no settings required.
Encryption starts during handshake: TLS 1.3 negotiates the secure session with forward secrecy via ECDHE. This means that even if someone intercepts your data later, they won’t be able to decrypt earlier sessions—like using a different encryption key for every conversation. Even if someone intercepts the traffic later, without the session key, they can’t decrypt it.
Protocols include:
- WireGuard: Fastest for general use; ideal for streaming and everyday browsing.
- Everest: Obfuscates VPN traffic to resist blocking in restrictive networks.
- OpenVPN-UDP: Legacy support for routers and enterprise compatibility.
Internal testing (Aug 2025) shows WireGuard maintains 90–95% of baseline speed, while Everest adapts best to unstable or censored environments.
Users can switch protocols in-app depending on speed, stability, or stealth needs.
No Logs, No Footprints—By Design
Many VPNs claim not to log data. X-VPN designs its infrastructure so it technically can’t.
What "No Logs" Actually Means
X-VPN states it does not store:
- IP addresses (incoming or VPN-assigned)
- Browsing history or URLs
- DNS queries
- Connection timestamps
But more importantly, the system itself avoids collecting them:
- All data passes through RAM-only servers, with no persistent storage.
- Session keys change with each connection. In other words, every time you connect—even to the same server—X-VPN resets your encryption keys to prevent reuse or exposure.
- Private DNS resolvers prevent third-party involvement. Instead of relying on your ISP or public resolvers, X-VPN answers domain lookups internally—so only X-VPN knows what sites you're trying to reach.
Since 2017, X-VPN has received over 239,000 legal or copyright data requests. None resulted in user data disclosure. (Source: X-VPN Transparency Report, Sep 2025)
What About Independent Audits?
As of late 2025, an external audit is in progress. While not yet public, users can already inspect technical claims via the Trust Center. For privacy-focused users, this level of transparency—even without third-party verification—sets a stronger baseline than silent promises.
How X-VPN Compares
Many mainstream VPN providers now offer no-logs claims, but the implementation varies. Some still rely on hard disk-based servers, which retain data until overwritten. Others lock key privacy features like Kill Switch or DNS leak protection behind paid tiers.
By contrast, X-VPN’s privacy model is available even to free users, and its in-memory infrastructure ensures nothing is stored—even temporarily.
A Privacy-Conscious Jurisdiction
Headquartered in Singapore, X-VPN operates under a legal regime independent from 5/9/14 Eyes surveillance alliances.
Many top-tier VPNs are based in data-sharing countries, which can mandate cooperation with intelligence networks. Singapore’s status offers fewer international disclosure obligations, reinforcing X-VPN’s ability to maintain no-logs integrity.
Combined with its zero-disclosure record and in-memory architecture, this makes X-VPN especially suited for users in politically sensitive or high-surveillance regions.
Free Plan, Same Core Protections
Many free VPNs come with trade-offs: aggressive tracking, bandwidth limits, or ads. X-VPN’s free tier is designed differently.
What Free Users Get
- Access to 1,000+ servers
- Manual region selection (26 locations on mobile)
- Kill Switch (on Android/iOS)
- Private DNS routing
- No signup required
- No email or phone number collected
According to the Free Plan Overview (Jul 2025), all traffic is encrypted and DNS-protected—even for users who never create an account.
That means casual users, students, and travelers can still benefit from real protections without handing over personal information.
About X-VPN
X-VPN is a privacy-first VPN service operated by LightningLink Networks PTE. LTD., based in Singapore. Trusted by over 100 million users worldwide, it runs 10,000+ RAM-only servers across 80+ countries. X-VPN applies AES-256 encryption, offers multiple protocols including WireGuard and Everest, and maintains a strict no-logs policy—all designed to provide verifiable privacy across all major platforms.